How to backup private keys
Table of Contents
What was holding me back from using pgp for a very long time was the fear of loosing my private keys and then not to be able to decode any messages sent to me. Also I didn’t feel comfortable storing a backup of my private keys in any place where they might easily be stolen.
tl;dr
pipe your private key through paperkey to dmtx and print a data matrix (QR-code) on paper
I strongly advertise against backing up relevant private keys in the cloud or on any digitally accessible medium.
The concept of paper wallets is well known in the crypto community where we have deterministic algorithms to recreate our wallets from a seed phrase. Unfortunately as of 2021 this is not possible with pgp keys (if it is please let me know @ rabbitholediaries@protonmail.com).
The next best thing to a pass phrase which is human readable is a QR code which is machine readable. In this tutorial I will guide you through the steps to backing up your private keys on paper and how to restore them.
Do you dare exporting your private key?
The first step is to export your private key from your key chain, which is something you usually don’t want to do. Especially not if you don’t know if you can trust the machine to not be compromised. If you already have an existing key, there is no way around this step, but you might want to consider the following proposal for any future keys you might want to create.
A proposal for keeping private keys private
In order to be able to truly trust that your keys are and remain safe I propose the following procedure:
- Create a new key on an airgapped computer running a non persistent OS - like Tails running on a Raspberry Pi.
- Print a paper backup as explained later in this article, to be able to restore the key as it will not be stored on any harddrive
- Transfer your key to cryptographic hardware like a Yubikey, Trezor or Smart Card. This way there is no remote access to your private key, other attack vectors might still apply.
To my knowledge this protects you from most, if not any, remote attacks trying to steal your keys.
The process
There are three steps involved, (1) exporting the key, (2) cleaning the output and (3) generating a machine readable image.
- is just specifying which key you want to export read about it in the gnupg manual
- using paperkey we can clean the output and strip everything non-essential to reduce amount of data we have to print. The code is open for review on github, but like me you will probably don’t take a look at it. I believe that’s fine if you follow my proposal and use an airgapped system, this way you only have to verify that the software does what it is supposed to (and you don’t have to verify that thats all the software does).
- Using the datamatrix utils dmtx-utils which are available on most package managers we encode the data in a machine readable QR code like matrix.
- As a heads-up: You will later need access to your public key to do a recovery, since paperkey removes this information from the gpg output.
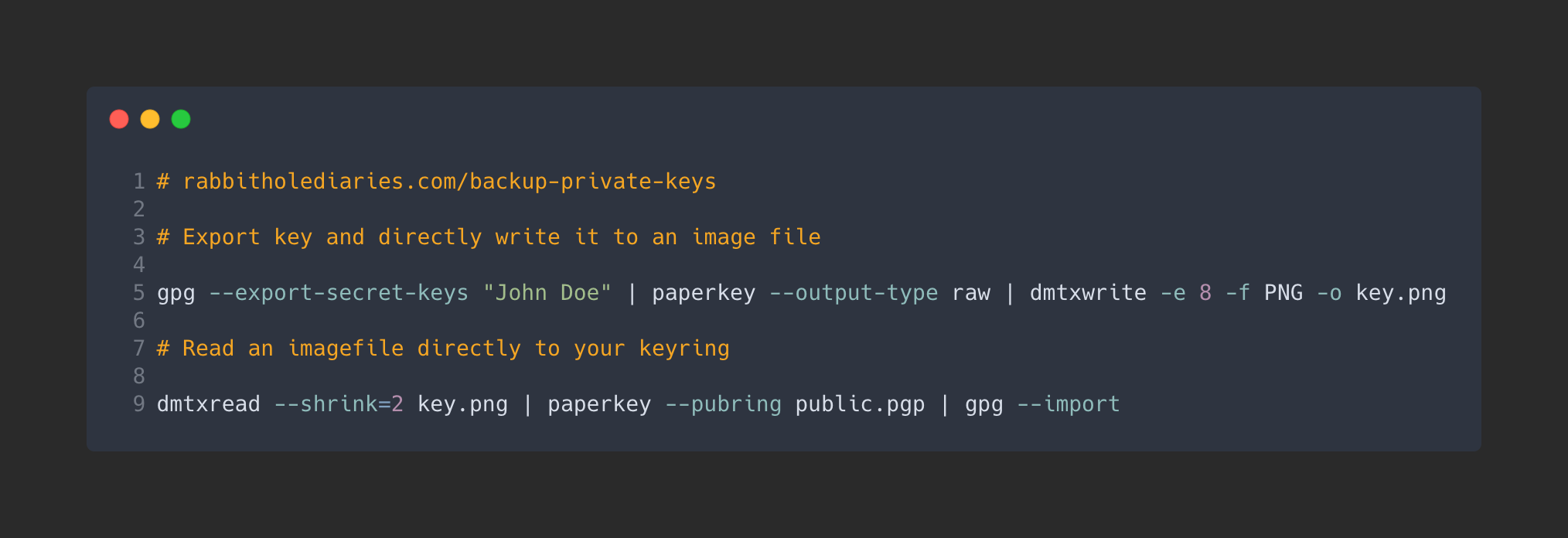
And because we don’t want to write our private keys to ‘disk’ we pipe the output from one command to the next like so:
# rabbitholediaries.com/backup-private-keys
# Export key and directly write it to an image file
gpg --export-secret-keys "John Doe" | paperkey --output-type raw | dmtxwrite -e 8 -f PNG -o key.png
# Read an imagefile directly to your keyring
dmtxread --shrink=2 key.png | paperkey --pubring public.pgp | gpg --importRecovering
The recovery process is basically the same in reverse with one caveat: You need access to the public key for your private key. As this information is considered “public” it was not encoded in the data matrix so you need to place your key in a public.pgp file on your computer to be able to recover your keys.
To verify that the data matrix you just created can in fact be used to recreate your private key go ahead and execute the command.
To increase your trust you should also print out the image, then scan it and run the import command again.
Due varying quality and resolution of scanners you may need to manually sharpen or blur the resulting image - this can in part also be achieved by altering/adding some dmtx-read arguments which you will find in this manual.
Having reliable pgp backups is possible - and for me paper is the medium of choice as it can sustain centuries but is also easy to destroy in case of “emergency”.
Did you follow along and created a paper backup? If so please share your story and let me know on twitter @rabbitholediary
Do you have a different take on backing up pgp keys?
I would love to have conversation either on twitter or send me an email at rabbitholediaries@protonmail.com.